Is that possible to MITM the Raspberry pi connection in our local network? Because I'm trying to learn how to intercept connection insiden LAN - Quora
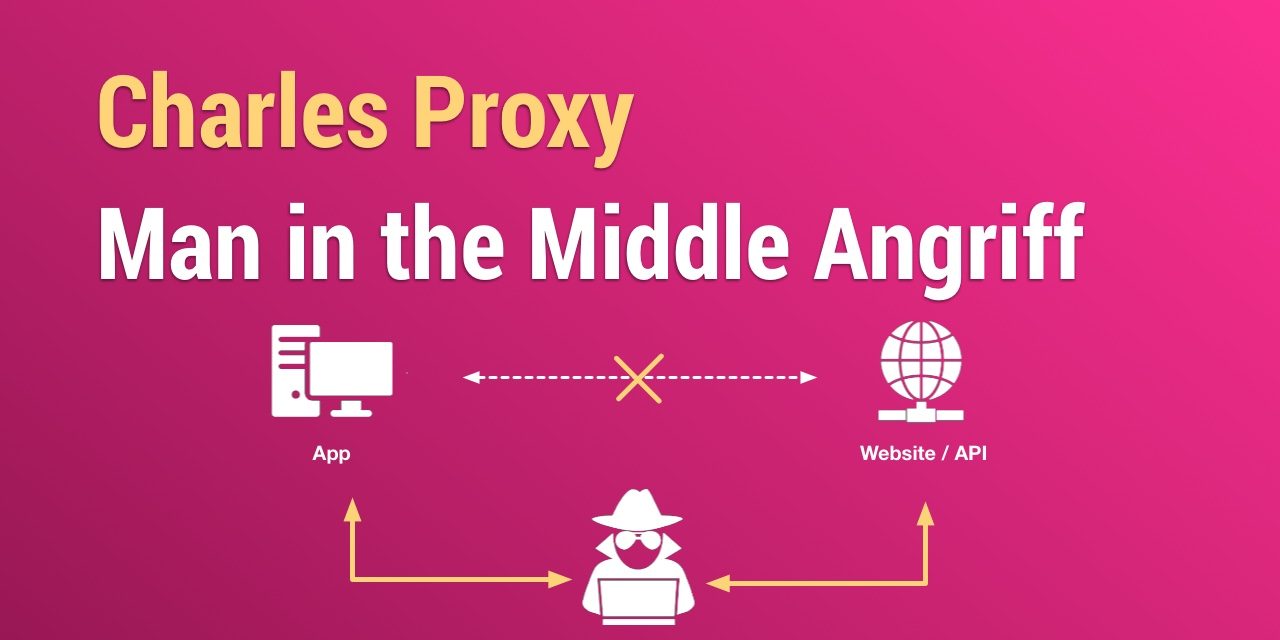
HTTPS Netzwerk Traffic von iOS Apps beobachten - Man in the Middle Attack ( MitM) - krannich Hausautomation

The MitM devices used in this paper. Top: Three 1Gbps Ethernet switches... | Download Scientific Diagram

Owning the Network with BadUSB. Man-in-the-Middle with a Raspberry Pi | by Jacob Baines | Tenable TechBlog | Medium

How to Build a Pumpkin Pi — The Rogue AP & MITM Framework That Fits in Your Pocket « Null Byte :: WonderHowTo