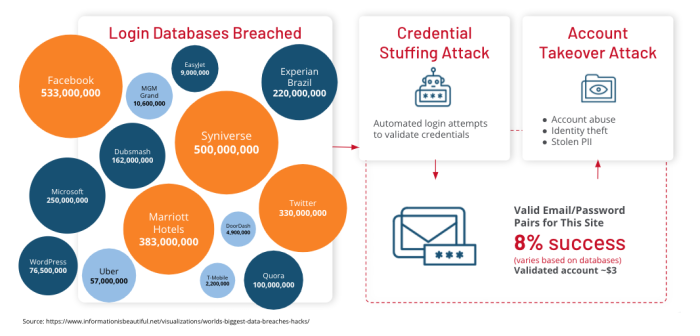
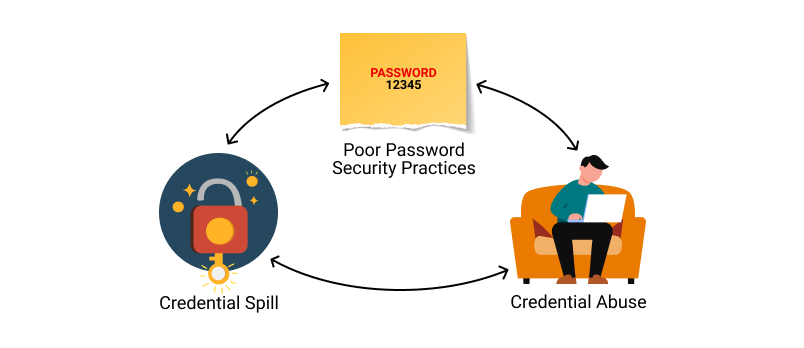
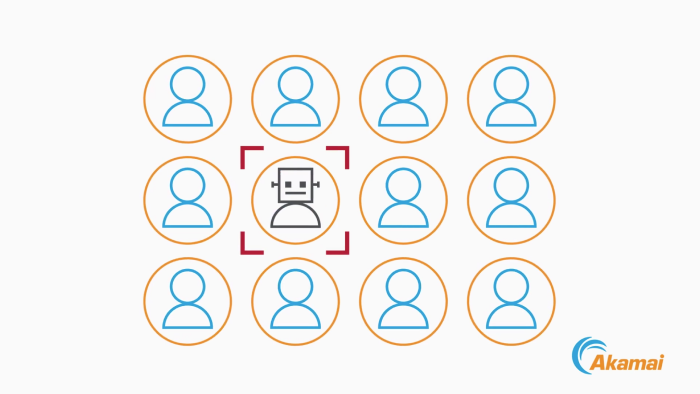
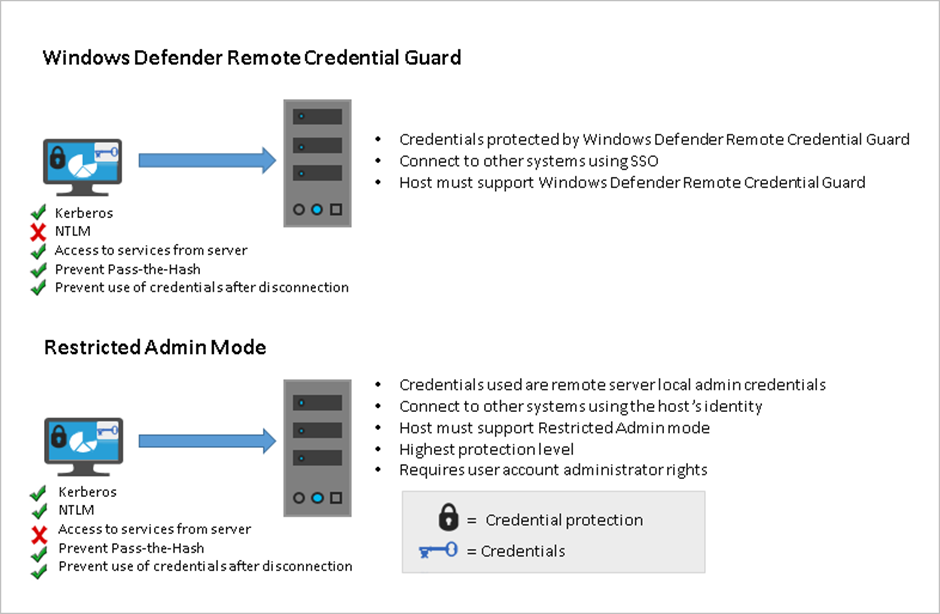
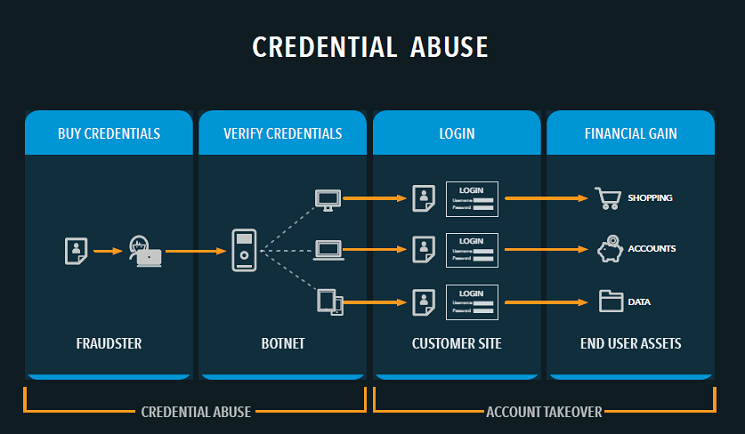
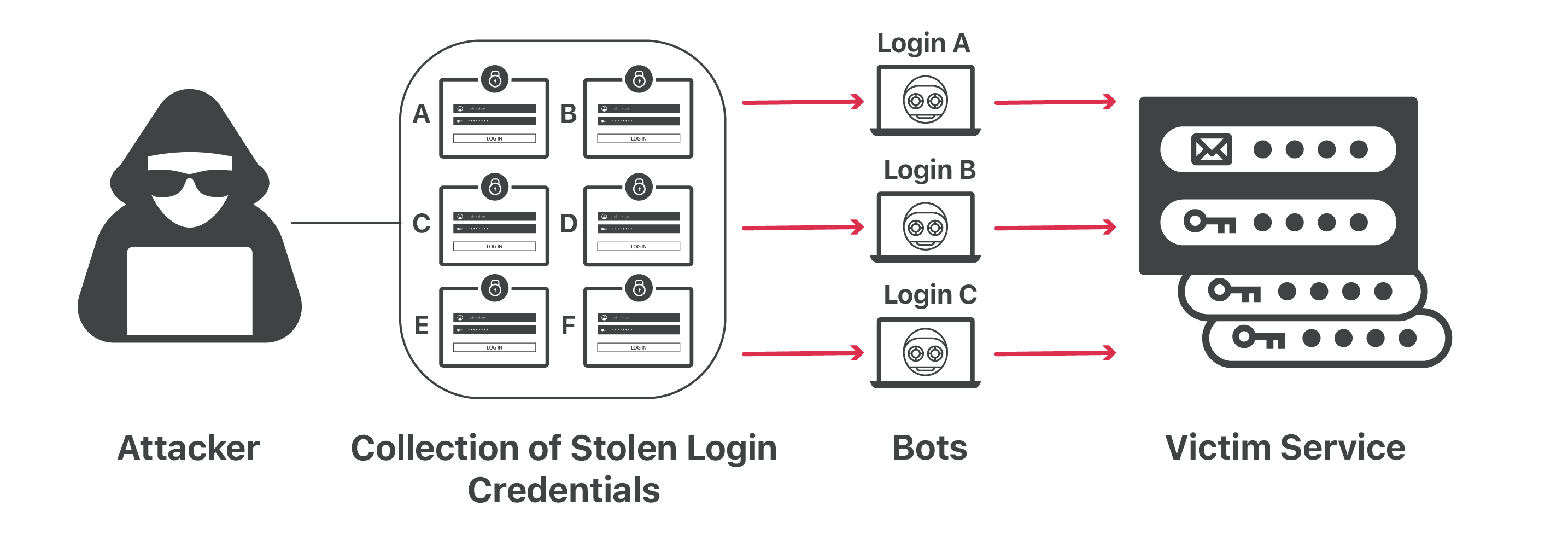
63 billion credential stuffing attacks hit retail, hospitality, travel industries - Help Net Security

Palo Alto Networks on Twitter: "Phishing & credential abuse 201: get inside the attack in today's Breach Prevention Week webinar https://t.co/utCwWQhGqm https://t.co/Ew3EuFHxIQ" / Twitter

Campaigns abusing corporate trusted infrastructure hunt for corporate credentials on ICS networks | Securelist