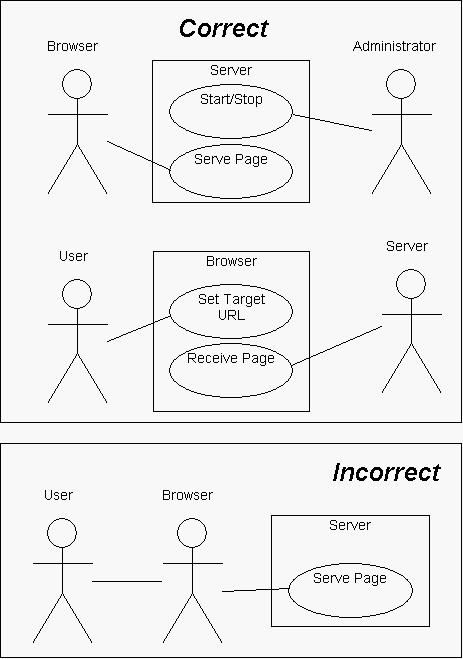
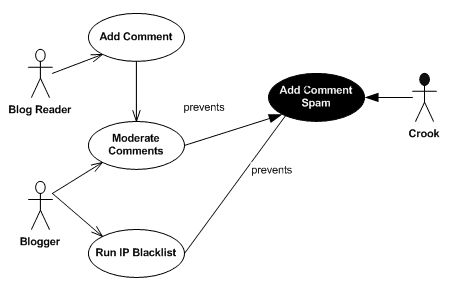
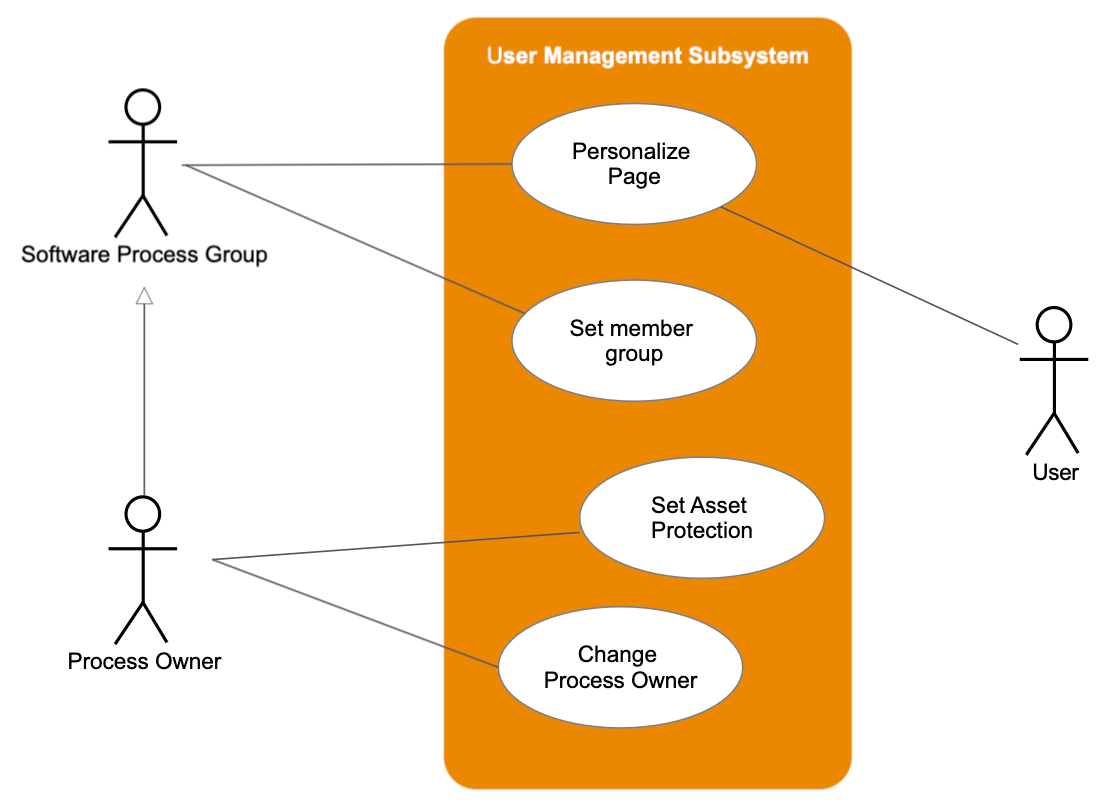
Figure 4 from Modelling misuse cases as a means of capturing security requirements | Semantic Scholar

Use/misuse-case diagram of car security requirements. Use-case elements... | Download Scientific Diagram

Experimental comparison of attack trees and misuse cases for security threat identification - ScienceDirect


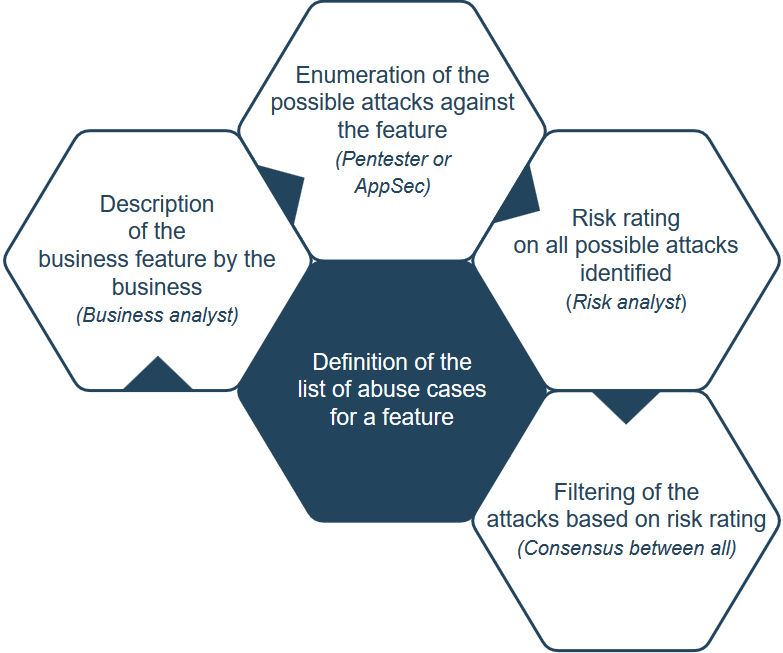


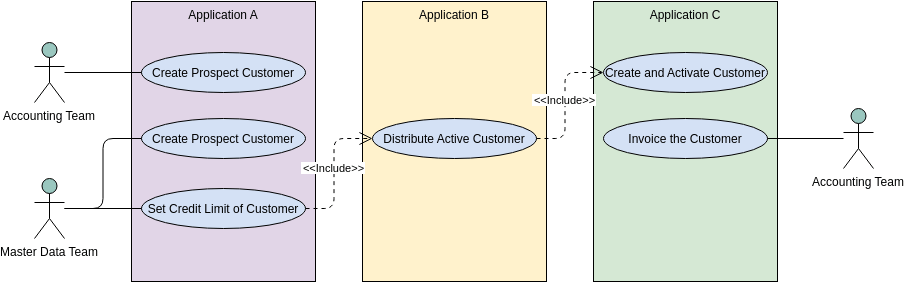



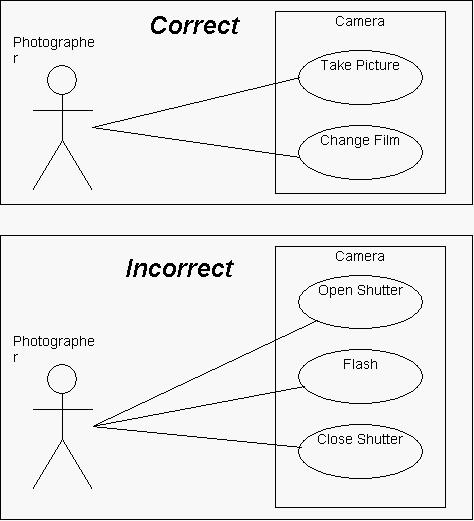
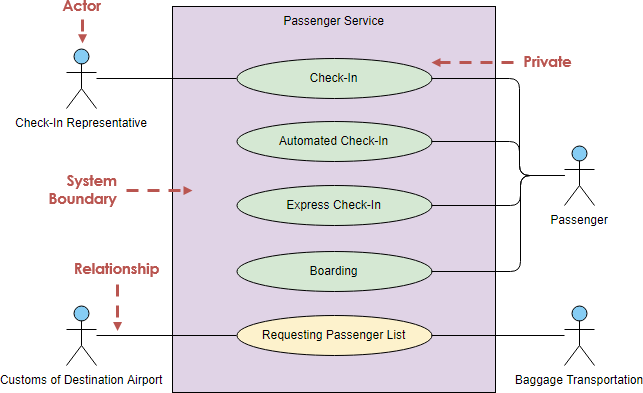
![PDF] Misuse Cases and Abuse Cases in Eliciting Security Requirements | Semantic Scholar PDF] Misuse Cases and Abuse Cases in Eliciting Security Requirements | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/de5bf979ba86304f50abea55ee7dcc032b098b8d/4-Figure2-1.png)